chromedshark
New Member
- Joined
- Apr 3, 2022
- Messages
- 33
TLDR: I'm looking for packet captures to confirm message checksum behavior and to verify behavior for other systems than a single AC300 + B300.
The AC300 (and other larger Bluetti devices) support both bluetooth and wifi for control. Bluetooth control does not require a pin, so anybody nearby could connect and control your device. Wifi control requires internet, and connects to Bluetti's server over an unencrypted connection. I want secure local control of my device(s), which means reversing the internet protocol and running my own compatible server (with eventual monitoring and a web interface for control).
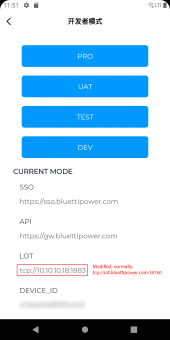
The Bluetti devices speak unencrypted MQTT v3.1.1 to iot.bluettipower.com on port 18760, with some non-standard extra message types used during the connection process. The device publishes to the topic "PUB/AC300/[device_serial_number_here]", and subscribes to a similarly named "SUB/..." topic. The payload appears to be a totally custom protocol revolving around reading from and updating 512 byte "pages" of data. The device regularly publishes updates to certain pages at a variety of offsets, and it can be polled more frequently for any data in any of the pages. The device is controlled by publishing updates to these pages through the "SUB/..." topic. All messages have a 2 byte checksum, and if it's wrong it will be ignored by the device.
I have managed to locate all the information the app displays, as well as figure out how to control everything the app does. There appears to be some detailed battery information that I haven't yet bothered to reverse, and there's a lot of extra fields that I have no clue on their purpose. I have some rough code up on Github, but my eventual goal is to re-write it all in Go so that it's easier to distribute and run. My eventual plan is a single solution MQTT server, metrics exporter (Prometheus), web api, and simple web interface for control and monitoring. The simplest deploy would be a raspberry pi running as an access point to simplify the DNS override, but if you wanted to you could deploy it wherever you wanted on your network. That said I've still got a ways to go to get there.
The one big thing holding me back right now is the message checksum. It's definitely a standard CRC16, but there's some kind of "prefix" that they're using that I haven't been able to figure out. I was able to bypass it for my device using a nice tool someone wrote, but if it's different per device then I'll need to write some code to calculate it before I can release anything. If I could get some packet captures of other people's devices, that would help immensely in figuring this out. WARNING: A full packet capture will include device passwords, which it might be possible to abuse, so I would recommend starting your capture after the device is connected to wifi. Additionally, if you go to the "About Device" section in the app, your device will send the current wifi ESSID it's connected to, as well as your wifi password, so I would stay away from that.
The AC300 (and other larger Bluetti devices) support both bluetooth and wifi for control. Bluetooth control does not require a pin, so anybody nearby could connect and control your device. Wifi control requires internet, and connects to Bluetti's server over an unencrypted connection. I want secure local control of my device(s), which means reversing the internet protocol and running my own compatible server (with eventual monitoring and a web interface for control).
The Bluetti devices speak unencrypted MQTT v3.1.1 to iot.bluettipower.com on port 18760, with some non-standard extra message types used during the connection process. The device publishes to the topic "PUB/AC300/[device_serial_number_here]", and subscribes to a similarly named "SUB/..." topic. The payload appears to be a totally custom protocol revolving around reading from and updating 512 byte "pages" of data. The device regularly publishes updates to certain pages at a variety of offsets, and it can be polled more frequently for any data in any of the pages. The device is controlled by publishing updates to these pages through the "SUB/..." topic. All messages have a 2 byte checksum, and if it's wrong it will be ignored by the device.
I have managed to locate all the information the app displays, as well as figure out how to control everything the app does. There appears to be some detailed battery information that I haven't yet bothered to reverse, and there's a lot of extra fields that I have no clue on their purpose. I have some rough code up on Github, but my eventual goal is to re-write it all in Go so that it's easier to distribute and run. My eventual plan is a single solution MQTT server, metrics exporter (Prometheus), web api, and simple web interface for control and monitoring. The simplest deploy would be a raspberry pi running as an access point to simplify the DNS override, but if you wanted to you could deploy it wherever you wanted on your network. That said I've still got a ways to go to get there.
The one big thing holding me back right now is the message checksum. It's definitely a standard CRC16, but there's some kind of "prefix" that they're using that I haven't been able to figure out. I was able to bypass it for my device using a nice tool someone wrote, but if it's different per device then I'll need to write some code to calculate it before I can release anything. If I could get some packet captures of other people's devices, that would help immensely in figuring this out. WARNING: A full packet capture will include device passwords, which it might be possible to abuse, so I would recommend starting your capture after the device is connected to wifi. Additionally, if you go to the "About Device" section in the app, your device will send the current wifi ESSID it's connected to, as well as your wifi password, so I would stay away from that.